TL;DR: By shifting security left with Octane, Button identified risks early, shipped cleaner code to auditors, avoided costly remediation cycles, and saved valuable engineering time. An Octane power user, Button also extended continuous automated security to its offchain Rust code.
How Button Made Smart Contract Audits Boring
TL;DR: By shifting security left with Octane, Button identified risks early, shipped cleaner code to auditors, avoided costly remediation cycles, and saved valuable engineering time. An Octane power user, Button also extended continuous automated security to its offchain Rust code.
Button is building onchain infrastructure that lets users borrow, earn, and trade while maintaining custody of their Bitcoin. Early in development, Button integrated Octane directly into its CI/CD pipeline to surface real issues as code was written, fix them immediately, and avoid costly surprises before launch.
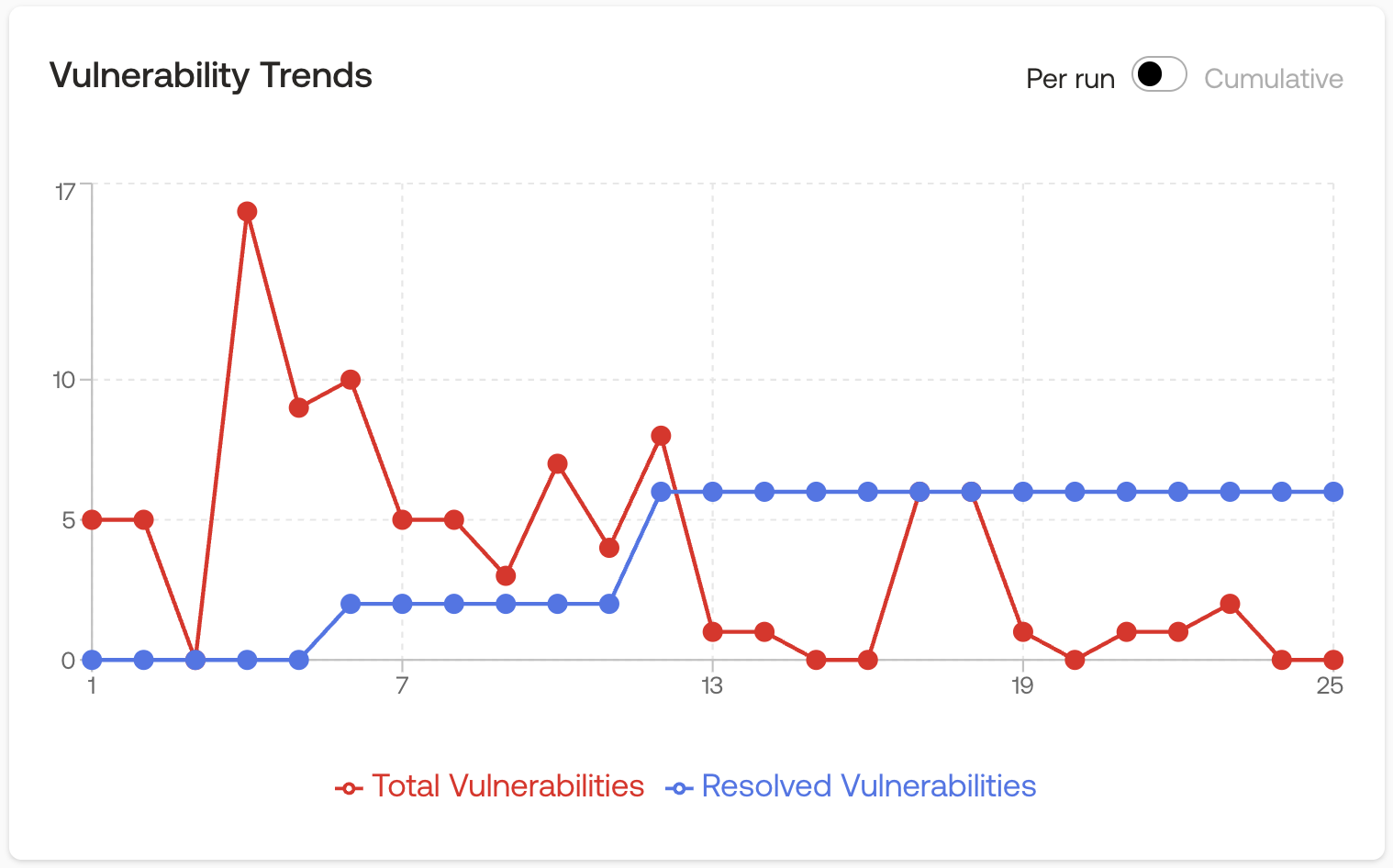
That decision quickly paid off. Button became an Octane power user, running a total of 25 scans during their pre-audit development process.
Building Button Better
This changed how the team built out Button:
- Security findings surfaced as code was written, not weeks later
- Engineers fixed issues immediately, while context was still fresh
- Design decisions were informed by real attack paths, not hypothetical risks
By integrating Octane into CI/CD, Button turned vulnerability detection and remediation into a routine part of development, rather than a high-stress, end-of-cycle event.
As a result of this shift-left security approach, when Button was ready for a manual security review, the codebase was already hardened and clean.
Auditors found no critical vulnerabilities, no high-severity issues, and only a single medium-severity finding, which Octane had already surfaced. Button sent cleaner code off for audit because Octane had already caught the meaningful risk during development.
.png)
Securing Offchain Rust Code
When we released a beta version of a language-agnostic Octane model, Button was one of the first teams to integrate the new tool into its offchain Rust codebase. This expanded continuous security coverage across another critical attack surface.
Security is now continuous and automated across Button’s onchain and offchain infrastructure. By unifying tooling across environments, Button strengthened the entire system and reduced risk across its entire stack.
Make Audits Boring With Octane
Button’s approach shows what’s possible when security is built into development instead of bolted on at the end. With Octane running continuously in CI/CD, teams can catch real issues early, send cleaner code to auditors, and avoid costly remediation cycles down the line.
If you want to save time, reduce security spend, and make your audits boring like Button, reach out today to see what Octane can find in your codebase.
FAQs
"Shift left” means you run smart contract security checks while the codebase is still in development, not just once it's done. Button integrated Octane into CI/CD so vulnerabilities could be surfaced on pull requests, engineers could fix them immediately, and design decisions were informed by real attack paths. The payoff is simple: you send auditors cleaner code, avoid late remediation work, and turn an audit from a potential crisis into a final confirmation.
Octane runs continuous security inside your CI/CD pipeline, meaning you can scan code changes as they land instead of waiting for a point in time audit. That keeps review tight around the actual diff, preserves developer context, and prevents security debt from compounding across weeks of commits. Button ran 25 scans pre audit, caught the meaningful risk early, and arrived at its final manual review with no criticals, no highs, and only one medium that Octane had already surfaced.
Octane is built for AI security for crypto across the stack, not just onchain contracts. Button extended automated security coverage to its offchain Rust codebase using Octane’s multi-language model, so security stayed continuous across both execution environments. That matters because real exploits often cross boundaries, where onchain assumptions meet offchain services, indexing, signing, or business logic.



